Dogs Save the Planet, Again
🟢 Infrastructure Week on the Blockchain
(Big Idea: Tokenomics)
Last issue we talked about Helium and their ambitious (?) use of tokens to bootstrap a wireless network. Two days after writing that, I read of a much simpler, more charming example of tokenomics involving Japanese manhole (personhole?) covers and adorable dog avatars.
The Japanese attention to detail is legendary so it’s not surprising that this extends to manhole covers. In the 1970s, customized, artistic manhole covers started appearing, the first of which featured “happy fish in water that had been cleaned by the sewer system.” Since then, manhole cover designs have expanded in quantity and creativity. There’s even an official Japanese Society of Manhole Lovers (I took one for the team and checked that the link is safe for work).
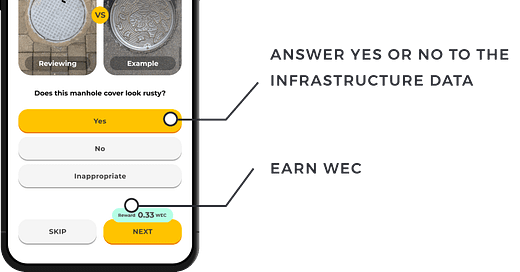
But, apparently, manholes get chipped and cracked and need repair or replacement more often than you might think. I’m told there are 15 million manhole covers in Japan, with 3 million currently at the end of their useful lives. So a non-profit launched an app called Tekkon that encourages people to upload geo-tagged photos of manhole covers in exchange for a cryptocurrency token (stirring demo video here). Players can earn tokens by uploading new photos or reviewing existing photos.
What can you do with these tokens? Users will soon be able to sell them, but why sell them when you can use them to level up your doggy avatar? You get gifted a pooch at the start, but from there, you need tokens to level up your Boo, unlock rare traits, purchase items or breed a new dog.
In their initial test, it took just three days to gather photos of each of the 10,500 manholes in Shibuya City, Tokyo. Since then, the app has accumulated over 1.1 million photos of manhole covers throughout the country in just over 6 months.
The next stop is utility poles, expansion in Asia and then even the U.S. The Tekkon team has grand visions of utilities, corporations and infrastructure providers harnessing their budding network to more efficiently maintain public goods. Is this likely to make it into the next U.S. Infrastructure Week? Perhaps not, but it’s a cool crowdsourcing experiment.
🟦 A Different Type of Hackathon
(Big Idea: Security)
Since last issue, we’ve seen two significant hacks in the crypto world. The headline values are notable: $570 million in one and $100 million in the second, but their mere occurrence has become almost commonplace. According to Chainalysis, 2022 is on pace to be the biggest year yet with $3 billion “grossed” over 125 hacks. Hooray for one metric that is up and to the right?!?
I tend to be a bit sanguine about these exploits as primarily a sign of market immaturity and growing pains versus an existential threat to crypto. Most hacks fall into two categories: technical hacks and what I might call “process hacks”. Technical hacks find a bug or oversight somewhere in the code and use that as an exploit. Process hacks take advantage of flaws or weaknesses in systems design. This week’s hacks represent one of each.
Binance is the world’s largest crypto exchange in terms of volume and is primarily focused on the Asian markets. They have their own chain, the Binance Smart Chain, which they basically control. Last weekend, an attacker sweet talked a Binance “Bridge” into sending them two transactions of 1,000,000 BNB coins, worth a total of around $560 million.
Due to their structure, bridges have been frequent targets of attacks (69% of funds stolen in 2022 so far have involved bridges). A bridge in crypto lets you move tokens from one crypto universe to another. For example, you can take your regular Bitcoin and “bridge” it to Etheruem, getting WBTC (wrapped Bitcoin) that you can use in the Ethereum world. Right now, there is about $5 billion of Bitcoin that has been locked up on one end of the bridge with an equivalent amount of synthetic Bitcoin, WBTC, generated on the other end. The Binance bridge is similar, allowing people to move assets between the Binance chain and other chains.
In the case of the Binance, the hacker exploited a bug in the bridge code that, essentially, didn’t pay enough attention to the details of how a transaction was proved to be genuine. The particular issue was a known weakness that had been fixed in subsequent versions. Basically, Binance was a bit sloppy.
But even if you manage to send yourself $560 million of coins, it takes a few more steps to turn that into a new Lambo. The hacker took their first 1M BNB coins and used them as collateral to borrow other coins and stablecoins (i.e. coins worth $1). They then bridged these coins out of the Binance world, into 6 different crypto universes. As people figured out what was going on, Binance stopped their entire chain to prevent more funds from leaking out (which also raised a ton of questions about how decentralized their chain could be if they could unilaterally just pause it). Tether, one of the biggest stablecoin providers, also blacklisted some of the funds. The best guess is that the hacker ended up with about $100 million. A huge haul, but also well short of the initial $560 million. The transparency of the blockchain again makes it harder than it seems to commit crimes (recall the Bitcoin hackers that stole $4.5 billion, but could only successfully launder 20% of that over the course of 4 years).
The second hack of the week, also involved interesting uses of collateral combined with some manipulation of an illiquid market. The hacker himself argues that it wasn’t really a hack, but just a “highly profitable trading strategy.”
Mango is a futures market on the Solana chain. The hacker deposited $5 million of stablecoins into account A and then offered 483 million perpetual futures. They then also funded account B with $5 million and bought those newly offered futures at a wildly inflated price (~9x where it had been). Suddenly, account A is sitting on an unrealized gain of $423 million. Apparently, that’s good enough to get a loan of $116 million from Mango these days. That loan then instantly cashed out effectively all of the liquidity that was left.
Even at the simplest level, this seems pretty preventable. When Harry the Hat walks into Cheers and starts asking for change, you should be suspicious. DeFi has some amazing use cases and capabilities, but that doesn’t mean that you don’t put any procedures in place. Sam Bankman Fried, who is a former Jane Street trader and now runs the FTX exchange, showed why having some experience is helpful. Their risk engine has a few pretty reasonable rules to prevent such issues. 1) If a price moves 3x in a minute, maybe it’s suspect so let’s bound the price feeds by 20% over a five minute period. 2) Weight your collateral calculations based on the size and liquidity of the collateral. If someone is trying to borrow literally 3 times the market cap of the thing they are using as collateral, maybe don’t do that.
Look, “Move fast and break things” works fine if you’re running an airport parking website or even a social network with just a few million people. But once your social network hits 100 million people, it’s a different equation. The same thing applies to crypto. It’s one thing if you’re breeding dog avatars in return for manhole cover photos, but if you’re running a decentralized perpetual futures exchange, it seems like you should have a higher bar for code review and risk policies. As the stakes rise, I think it is reasonable to think that we will see more attention paid to details and corner cases.
It’s notable that the bigger market cap, higher visibility projects seem to have fewer hacks. Smaller Bitcoin exchanges once saw occasional hacks, but they've stepped up their game and that now seems to be a thing of the past (knock on wood). Mango Markets clearly is not Coinbase.
All of crypto is kind of a giant bug bonus. If you could figure out how to hack Bitcoin to create 100,000, a $200 million windfall is a pretty big incentive. The fact that core Bitcoin hasn’t been hacked yet doesn’t mean that it never will be, but each day that goes by with that bug bonus not having been redeemed makes it more likely that it never will be.
In the meantime, all of these hacks build scar tissue that will likely be beneficial as crypto scales. It helps identify general areas of weakness, puts more pressure on developers to be thoughtful and diligent in their coding and makes a stronger argument for strict auditing.
◆ Zero Knowledge Is Good?
(Big Idea: Crypto Technology)
I still think crypto is underestimated, in part, because the technology is obscure enough that people don’t understand how unique it is and how transformative it can be. One of my goals with this newsletter is to help explain that in small ways so let’s wrap up today with a quick primer on Zero Knowledge (ZK) Proofs.
ZK proofs allow you to validate a piece of information without exposing any data to prove it. You basically “prove” something is true without doing anything more than verifying it is true. That sounds weird and slightly unbelievable, I know. But here are some examples.
How do one prove that they are old enough to buy liquor? Currently, they hand over their driver’s license with their full birthdate, home address, eye color, etc. The bouncer or grocery store clerk then, with varying degrees of efforts, tries to make sure the ID is real, does math on the birthdate and then proceeds. Or, if it’s FedEx delivering a box of wine, they actually scan your ID into some black hole of a database which surely would never used for other purposes. Instead, with a zero knowledge proof, the “witness” could answer the “challenge” that they are over 21 without revealing any additional information and the “verifier” can accept it to be true.
Or, let’s say you’re launching an awesome crypto hedge fund and you need your investors to prove that they are accredited investors. Currently, that process involves sharing pay stubs or tax forms or bank statements, each of which contain highly sensitive information, well beyond the yes/no question being asked. Again, a ZK proof could verify that the investor meets the criteria without revealing one’s total net worth or annual salary.
How ZK proofs work is a bit beyond the scope of this newsletter, but it’s one of those concepts that is a bit mind blowing that it can work. The first zero knowledge proofs were developed in the 80s and the mathematics and sophistication have grown massively. For a long time, the computing was cost prohibitive at scale, but now those have massively improved as well. Beyond uses to preserve privacy, Layer 2 solutions using ZK-SNARKS are starting to launch to greatly expand Ethereum capacity. If history is any guide, there will be thousands of uses that we may have never expected as ZK proofs create another building block to layer on top of.
This Week's Burning Hot Take
“Is the home computer destined to become the CD of the ‘80s, the hula hoop of the ‘80s?”
Michael Dertouzos on NBC’s Today Show, August 8, 1983.
As always, thanks for reading. Send me questions and please share with your crypto curious friends.